Blog







Anoma XAN Airdrop: Registration is Now Open
Check your eligibility and register now for season 1 of the Anoma XAN airdrop.








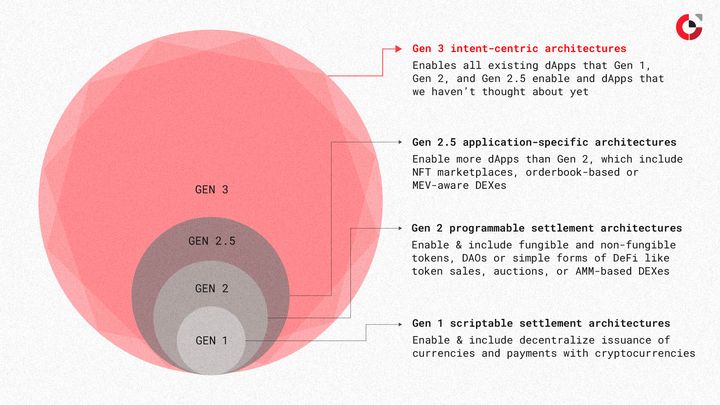











Intent-based protocols pt1: unfolding UniswapX
In part 1 of our series on intent-based protocols, we break down UniswapX.


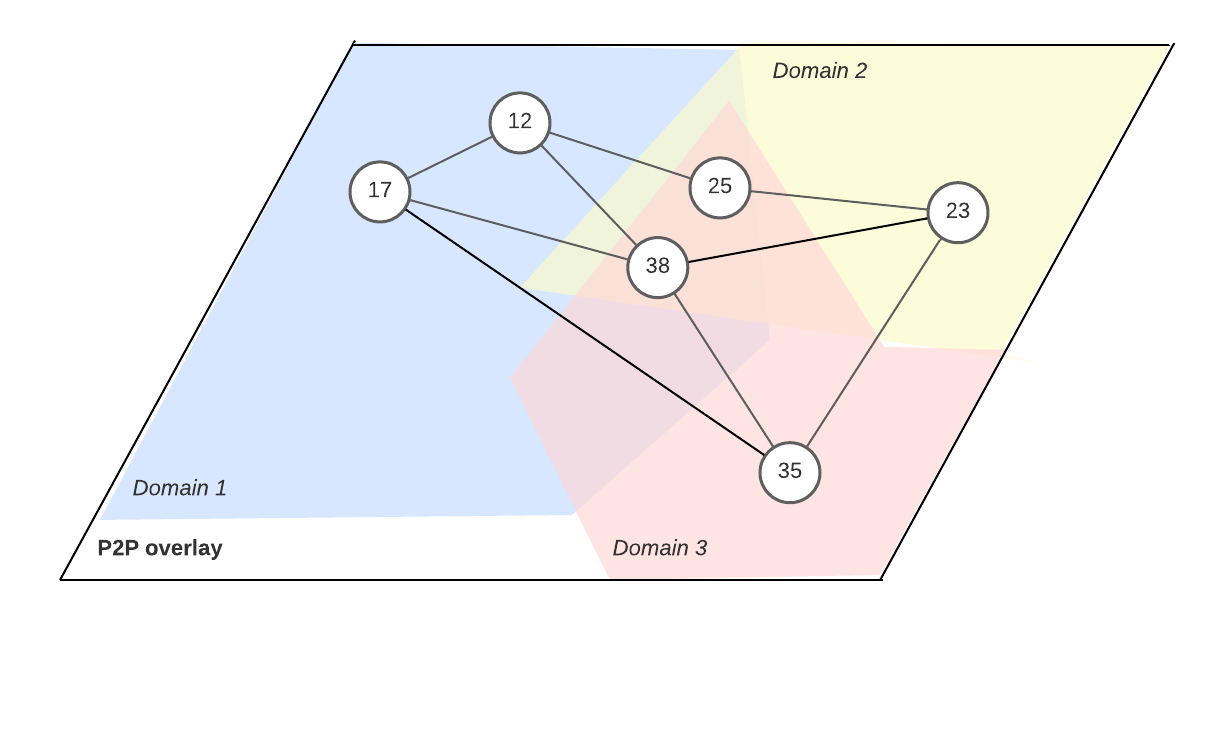
This is not the SUAVE you are looking for
In our follow-up to intent-based protocols pt.1 we examine SUAVE - a marketplace for MEV mechanisms.